Project AI4TrustBC
Abstract
 BlockChain (BC) (introduced in the white paper by Nakamoto, 2008) is a specially designed data storage structure, maintained without any third party of absolute trust. The first BC implementation was related to the financial domain - performing transactions with Bitcoin cryptocurrency. BC could be regarded as a public ledger where all data (referred to as "committed transactions") are stored in a list of blocks (Zheng et al, 2017). New data (organized in blocks) from different domains (cryptocurrency/finance, digital identity, voting, notary, smart contracts, IoT, insurance, healthcare, etc.) are allowed to be added simultaneously. Only blocks verified by the agreement between a given number of agents (entities, nodes) could be added to the chain and they cannot be changed anymore (they remain immutable). The core property of BC is that validation of the blocks to be added is performed without involving a so-called "third party of absolute trust", while the immutability and security is ensured by cryptology techniques. Verification of data without "trusted third parties" is realized by the so-called consensus protocols most of which are based on cryptology techniques.
BlockChain (BC) (introduced in the white paper by Nakamoto, 2008) is a specially designed data storage structure, maintained without any third party of absolute trust. The first BC implementation was related to the financial domain - performing transactions with Bitcoin cryptocurrency. BC could be regarded as a public ledger where all data (referred to as "committed transactions") are stored in a list of blocks (Zheng et al, 2017). New data (organized in blocks) from different domains (cryptocurrency/finance, digital identity, voting, notary, smart contracts, IoT, insurance, healthcare, etc.) are allowed to be added simultaneously. Only blocks verified by the agreement between a given number of agents (entities, nodes) could be added to the chain and they cannot be changed anymore (they remain immutable). The core property of BC is that validation of the blocks to be added is performed without involving a so-called "third party of absolute trust", while the immutability and security is ensured by cryptology techniques. Verification of data without "trusted third parties" is realized by the so-called consensus protocols most of which are based on cryptology techniques.
BC is basically a distributed system (distributed ledger) that can be centralized or decentralized. It means that this ledger is spread across the network, and each of the network partners holds a copy of the complete ledger. In this distributed system nodes can be defined as individual players, and messages can be sent and received between them. As having memory and processor nodes, BC can become a subject of dishonest user attitude, being damaged or become dangerous itself. Therefore, the problem of distributed consensus in the network without trust arose.
- It is managed autonomously, without third authority.
- It removes the possibility of infinite reproducibility from a digital asset, i.e., it confirms that each unit of value was transferred only once, solving the long-standing problem of resource wasting by doubling data.
- It can assign title rights to agents by properly setting the exchange agreement between the agents that will cooperate to outpace attackers.
The consensus algorithm is responsible for maintaining the integrity and security of the whole BC based system. Any BC system has a distributed structure and does not rely on a central authority. The consensus protocol is employed in order to provide the validity of transactions. In other words, validity of a transaction should become common knowledge of all agents. Therefore, one of the crucial properties in the BC consensus protocol is to guarantee that in every execution step consensus is achieved and that all transactions occur in a trustful way. Consequently, the reliability and security of the consensus protocols appear as the top importance issues. A lot of consensus protocols are based on certain cryptographic puzzles related to the inversion of one-way functions noting that beside a traditional hash function, other one-way functions could be employed particularly taking into account advances in this topic (see, as an illustration Mihaljevic, 2019). When the consensus protocol is based on solving a cryptographic puzzle, it could be performed by spending certain computational resources, i.e., performing some work, and these protocols are denoted as Proof-of-Work ones.
When the consensus protocol is based on the Proof-of-Work paradigm, the basic steps of the protocol are as follows:
- New transactions are broadcast to all agents.
- Each agent collects a subset of new transactions into a block.
- To verify its block, the agent has to solve a difficult Proof-of-Work task for that block.
- When an agent solves a Proof-of-Work, it broadcasts the block and the solution to all agents.
- Agents verify a Proof-of-Work, validity of transactions in the block, and their uniqueness and accept the block if all verifications passed. Otherwise, block is rejected.
- The accepted block is added to the end of chain, together with the hash that would be used to verify the upcoming blocks.
It could happen that two agents broadcast different versions of the next block simultaneously, and branching occurs in the chain. The longest chain, i.e., the one containing the most Proofs-of-Work, is favored, it is considered to be the correct one and all agents will keep working on extending it.
The main task in designing and implementing BC is to ensure the consistency of distributed data, i.e., that each copy of a data contains the same value. Another important task is to disable the analysis and knowledge discovery of recorded data that would raise the privacy issues and compromise the entire system. Consequently, the evaluation of the system security is one of the essential tasks that should engage advanced approaches and techniques, which, on the other hand, should provide basis for the construction of safer components of the BC based systems.
Artificial Intelligence (AI) and BC are proven to be quite a powerful combination, improving virtually every industry in which they’re implemented. Recently, it has been acknowledged that artificial intelligence techniques can be of significant importance for the evaluation of components and entire BC systems (Marinković et al, 2019; Salah et al, 2019). AI can effectively mine through a huge dataset to create newer scenarios and discover patterns based on data behavior. Therefore, the goal of this project is to provide contribution to the application of artificial intelligence in the BC technology domain:
- Knowledge reasoning techniques can be used to analyze consistency of consensus algorithms for BC.
- Employment of AI techniques for the analysis of anonymous data in order to evaluate robustness of the privacy protection in certain BC ledgers.
The project would deal with the open problems that have arisen due to the rapid technological breakdown and would explore new artificial intelligence techniques for presenting and discovering knowledge, managing privacy, ensuring consistency and reliability of modern BC technology. Within this project we propose to develop and use knowledge reasoning techniques based on formal methods, non-classical logics, and metaheurists (the fields of expertise of the project team members) to deal with the above mentioned challenges. The main research goal would encompass the implementation and performance examination of the BC systems with incorporated the above mentioned artificial intelligence techniques and their comparison with classical BC implementations.
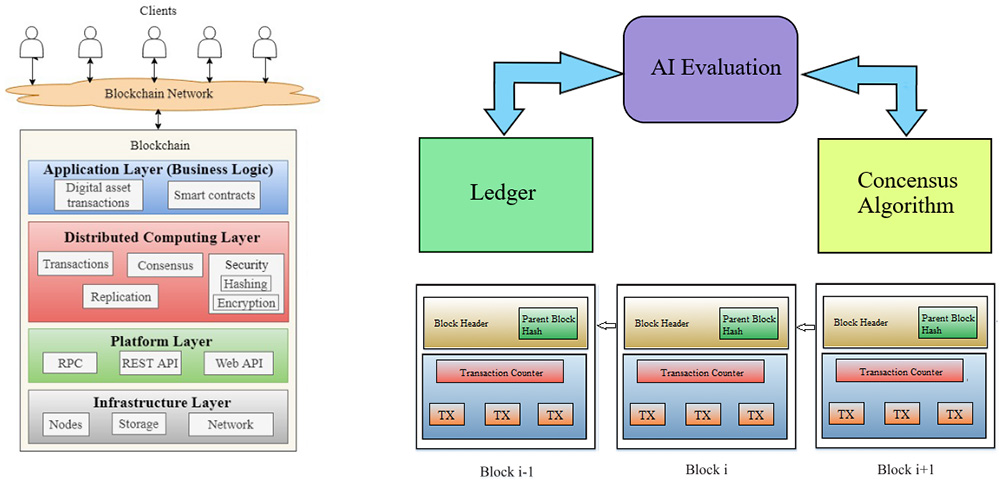
The structure of BC and AI involvement are illustrated in next Figure.
References:
- S. Nakamoto: Bitcoin: A peer-to-peer electronic cash system, Pseudonymous posting (2008). Archived at https://bitcoin.org/en/bitcoin-paper.
- Z. Zheng et al. "An overview of blockchain technology: Architecture, consensus, and future trends." Big Data (BigData Congress), 2017 IEEE International Congress on. IEEE, 2017.
- M. J. Mihaljevic, "A Security Enhanced Encryption Scheme and Evaluation of Its Cryptographic Security", Entropy, vol. 21 (7), July 2019 (11 pages)
- B. Marinković, P. Glavan, Z. Ognjanović, T. Studer, A Temporal Epistemic Logic with a Non-rigid Set of Agents for Analyzing the Blockchain protocol, Journal of logic and computation, 29(5), 803-830, (2019).
- K. Salah, M. Habib Ur Rehman, N. Nizamuddin, and A. Al-Fuqaha, "Blockchain for AI: Review and Open Research Challenges", IEEE Access, 2019.


 BlockChain (BC) (introduced in the white paper by Nakamoto, 2008) is a specially designed data storage structure, maintained without any third party of absolute trust. The first BC implementation was related to the financial domain - performing transactions with Bitcoin cryptocurrency. BC could be regarded as a public ledger where all data (referred to as "committed transactions") are stored in a list of blocks (Zheng et al, 2017). New data (organized in blocks) from different domains (cryptocurrency/finance, digital identity, voting, notary, smart contracts, IoT, insurance, healthcare, etc.) are allowed to be added simultaneously. Only blocks verified by the agreement between a given number of agents (entities, nodes) could be added to the chain and they cannot be changed anymore (they remain immutable). The core property of BC is that validation of the blocks to be added is performed without involving a so-called "third party of absolute trust", while the immutability and security is ensured by cryptology techniques. Verification of data without "trusted third parties" is realized by the so-called consensus protocols most of which are based on cryptology techniques.
BlockChain (BC) (introduced in the white paper by Nakamoto, 2008) is a specially designed data storage structure, maintained without any third party of absolute trust. The first BC implementation was related to the financial domain - performing transactions with Bitcoin cryptocurrency. BC could be regarded as a public ledger where all data (referred to as "committed transactions") are stored in a list of blocks (Zheng et al, 2017). New data (organized in blocks) from different domains (cryptocurrency/finance, digital identity, voting, notary, smart contracts, IoT, insurance, healthcare, etc.) are allowed to be added simultaneously. Only blocks verified by the agreement between a given number of agents (entities, nodes) could be added to the chain and they cannot be changed anymore (they remain immutable). The core property of BC is that validation of the blocks to be added is performed without involving a so-called "third party of absolute trust", while the immutability and security is ensured by cryptology techniques. Verification of data without "trusted third parties" is realized by the so-called consensus protocols most of which are based on cryptology techniques.
